WHAT IS CRYPTOGRAPHY?
Cryptography is an essential aspect of securing information. It is a technique for information protection and inter-party communication using codes. This technique is derived from mathematical concepts and ensures that when a message is sent, only authorized persons for whom the message is intended can read it. Thus, it prevents unauthorized access to information.
PURPOSE OF CRYPTOGRAPHY?
Nowadays, the Internet is helping millions of people exchange information in real-time and has become an essential part of everyday life. It is used as a tool for commerce, online banking, finance and social networking. Due to the exchange of an increasing amount of personal information and sensitive data, security has become a key issue for everyone to deal with. Hence, cryptography is necessary when communicating over any untrusted medium, which includes just about any network, particularly the Internet. Within the context of any application-to-application communication, there are some specific security requirements, including:
- Authentication: Process to prove one's identity
- Privacy/confidentiality: Ensuring that no one can read a message except the intended receiver
- Integrity: Assuring the receiver that the received message has not been changed in any way from the original
Cryptography, not only protects data from theft or alteration but can also be used for user authentication.
Types of Cryptography:
- Symmetric key cryptography, also known as secret key encryption, entails encoding plain text with a secret key. Decryption requires knowledge of the same secret key.
ciphertext = encrypt(plaintext, symmetric key)
plaintext = decrypt(ciphertext, symmetric key)
Symmetric key cryptography is useful and solves a wide range of problems. It is relatively faster than asymmetric key encryption. The biggest problem with symmetric key encryption is sharing the secret key with the recipient (key distribution problem). Securely communicating the encryption key to the receiver is sometimes almost as hard as securely communicating plain text.
Another problem is that a large number of key pairs are required between different communicating parties. Thus, it becomes very difficult to manage if the number of participants grows. If n is the number of participants, the key pairs required would be n(n-1)/2.
For example: If 5 parties want to communicate with each other then 5(5–1)/2 = 20 different key pairs are needed. This would increase to 1225 for 50 participants and 4950 if there are 100 participants.
The most widely used symmetric algorithms are Caesar cipher, Data Encryption Standard (DES), SDES, 3DES, Advanced encryption standard (AES), Blowfish, IDEA, RC4, RC5, RC6, etc.
Symmetric key cryptography leaves us with the problem of key distribution. Public-key cryptography addresses the problem of how to communicate the key securely.
- Asymmetric key cryptography, better known as public-key cryptography, provisions two keys known as a key pair:
- A private key or secret key is only available with you (and must be kept a secret).
- The public key is available to anyone who might want to send you a message. Two of the best-known uses of public-key cryptography are Public Key Encryption and Digital Signatures.
2.1 Public key encryption: A message is encrypted with the recipient’s public key and the recipient uses his/her private key to decrypt the message.
ciphertext = encrypt(plaintext, Public Key)
plaintext = decrypt(ciphertext, Private Key)
When a Sender wants to send a message to a Receiver, using this method:
- Sender obtains the Receiver’s public key
- The sender encrypts the message with the Receiver’s public key and sends it
- The receiver decrypts the message with his/her private key
Public key encryption has far better success in ensuring the security of information transmitted during communication. It guarantees that a message that is encrypted using the Recipient’s public key can only be decrypted using the corresponding private key.
Security of the public key is not required because it is publicly available and can be shared over the internet. It is impossible to decrypt a message using the Recipient’s public key or to derive the Recipient’s private key from the public key. Therefore, even if the message and Recipient’s public key fall into hostile hands, the message cannot be decrypted (since the private key cannot be determined).
2.2 Digital Signatures: Before we understand Digital Signatures, let us take a quick look at hash functions:
Hash functions, also called message digests and one-way encryption, are algorithms that, in essence, use no key. Instead, a fixed-length hash value is computed based upon the plaintext that makes it impossible for either the contents or length of the plaintext to be recovered. Few popular hashing algorithms are MD2, MD4, MD5, SHA1, LANMAN, etc. These hash functions are used in Digital Signatures cryptography, as explained below.
When a Sender wants to send a message using Digital Signatures, the following steps are executed:
1. Calculate Message Digest — In the first step of the process, hash value is calculated from the message by applying a cryptographic hashing algorithm like MD5.
2. Calculate Digital Signature — In the second step of digitally signing a message, the message digest obtained in the first step is encrypted with the private key of the sender and then an encrypted hash value is obtained, also called Digital Signature.
When the Receiver receives the encrypted message, verification of Digital Signature is performed in three steps:
1. Calculate Current Hash Value — On the Receiver’s end, hash value of signed message is calculated again. It is important to use same hashing algorithm used during the signing process. This hash value is called Current hash value because it is calculated from the received message.
2. Calculate Original Hash Value — Decryption of digital signature is carried out with same encryption algorithm that was used during the signing process. The decryption is done using the Sender’s public key. After decryption, the Original hash value (calculated from the original message) is obtained.
3. Compare the Current and the Original Hash Values — finally; the Current hash value is compared with the Original hash value.
- If the two values are identical, the verification successfully proves that the message has been signed with the private key of the Sender (whose public key was used in the verification process).
- If the two values differ, this means that the digital signature is invalid and the verification is unsuccessful.
Popular asymmetric key cryptography algorithms are RSA, DSA, Elliptic curve, PKCS, Elgamal, etc.
Problems in secure Public key distribution
When a key pair is generated, you need to keep the private key part a secret while the Public key can be distributed freely. If a Sender wants to send an encrypted message to Receiver, he/she can encrypt it using the Receiver’s public key.
How can the Sender reliably find out the Receiver’s public key? If an intruder persuades the Sender that some other key is the Receiver’s public key, then he can launch a man-in-the-middle attack. When the Sender sends a message encrypting it with the “fake Public key”, the intruder decrypts it using the corresponding “fake Private key”, reads /modifies it, encrypts it again with the receiver’s real public key, and sends it onwards. Neither the Sender nor the Receiver will be aware of the MITM attack.
The figure below shows an example of a MITM attack:
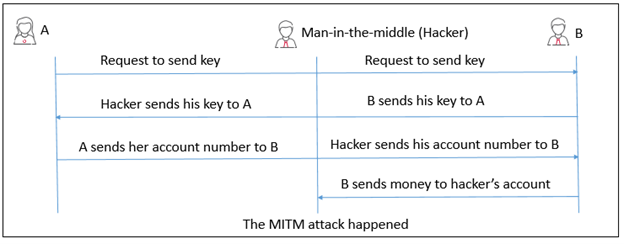
Man-in-the-middle attack will also enable the intruder to sign messages on the Receiver’s behalf. Since everyone thinks the “fake Public key” is the Receiver’s Public key, any messages signed by the intruder using the corresponding “fake Private key” will be accepted as messages sent by the Receiver.
Therefore, public key cryptography depends on the ability of users to be sure of each other’s public keys. In general, distribution via the web is not secure enough, since emails and web pages can be hacked. A variety of techniques such as HTTP Public key pinning, Domain Name System Security Extensions (DNSSEC) can help defend against MITM attacks.
Summary
Every piece of information, that passes through a computer network is not secure. Multiple cryptographic techniques have been devised for authentication, to protect sensitive information, maintain data integrity and allow safe and secure communication.
Public key cryptography addresses the key distribution problem and is more secure as compared to Secret key algorithm. However, Secret key cryptography is much faster than Public key cryptography. Hash functions, are well suited for ensuring data integrity because any change made to the message will result in the receiver calculating a different hash value than the one placed in the transmission by the sender.
It is hard to say which technique is better than others; the decision should be made based on your application. Whatever technique you use, security is a must in every data exchange, because as we all know “Attacks only get better, never get worse.”